ReadELF Reverse Engineered Replication
This project was an extension of an assignment for my Software Reverse Engineering class (EE 491F). Software reverse engineering requires extensive knowledge of software engineering, and this project perfectly demonstrates this. In order to successfully create the ReadELF program, one must first have detailed knowledge about the ELF file system - the format of the ELF and section headers, what type of content can be stored in these headers, and how these change based the computer they were compiled on (32bit vs 64bit addressing, and little vs big endian). In order to utilize this knowledge in recreating the ReadELF program, extensive knowledge of C programming is required. This project pushed me to grow as a programmer both in my technical coding knowledge and in my understanding of what it takes for a progam to actually execute.
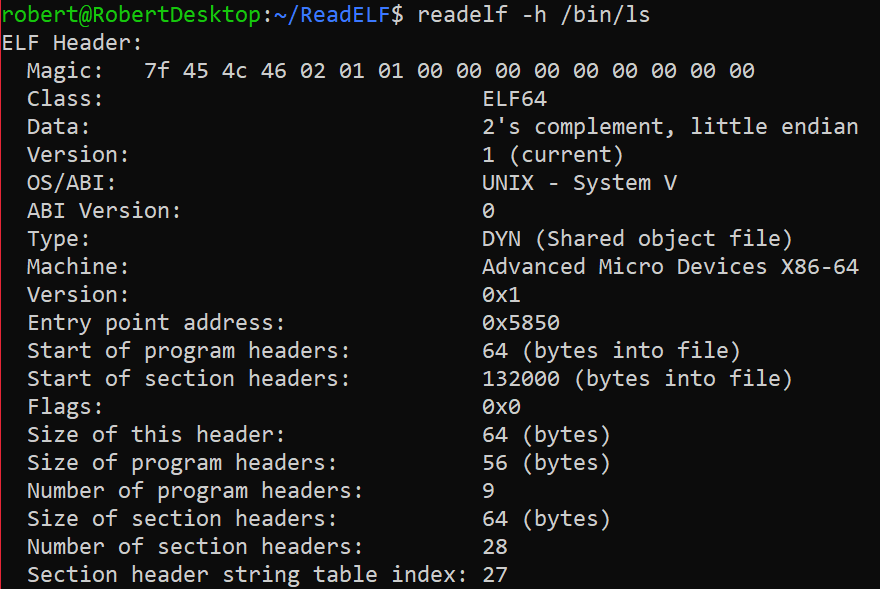
Linux’s ReadELF Output
The following output is a result of running Linux’s ReadELF command on the ls ELF flie:
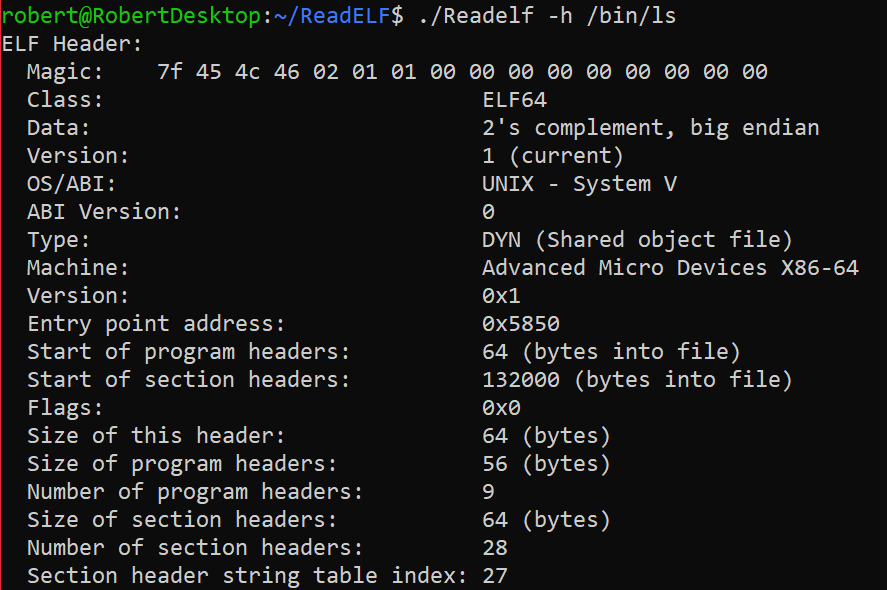
My ReadELF Output
The following output is a result of running my replicated ReadELF command on the ls ELF flie:
Endian Detection Code Excerpt
The following code is used to check whether a local machine is little endian or big endian. By storing 1 in an int n, we can cast the int’s pointer to a
character pointer to limit it to a single byte (from most machine’s 4-byte int size). If we dereference this single byte, we will get a value of 1 if the
local machine is little endian, since the one is stored in the rightmost byte. Otherwise, we know the machine is big endian.
int n = 1;
int localEndian;
// Check local endianness
if ( *(char *)&n == 1 ) {
localEndian = ENDIAN_LITTLE;
} else {
localEndian = ENDIAN_BIG;
}
You can view the whole code in the GitHub repository for this project.